What Are the Best Ways to Manage Visitors? | Greetly
The pros and cons of different visitor management systems so you can determine the perfect plan for your workspace.
What are visitor management techniques and steps? Follow this guide to impress your guests like a Fortune 500 company -- on a bootstrapped budget.
Every business and organization has visitors. Some just get a few packages and food deliveries. Others have customers, vendors, and interview candidates streaming in and out all day. How offices manage visitors can be as varied as the organizations themselves. For some, the process of visitor check-in is regimented and formal. For others, handling guests is a fly-by-the-seat-of-the-pants affair.
Regardless of the visitor management system, there are certain aspects to the process of handling guests that are common across the board. Most are done so quickly that sometimes very little thought goes into the process at all. Each step, however, is important to the functioning of your organization, the safety of your employees and data, the comfort of the guest, and -- most importantly -- the overall efficiency of time spent.
In this six-part article about the visitor management process, we’ll break down each step of the process, explain why it is important, and give examples of different methods for effectively accomplishing the end goal - great first impressions, productivity, and safety.
 Here are the six most important visitor management techniques:
Here are the six most important visitor management techniques:

 Have you ever walked into a restaurant or other place of business, looked around, and had no idea what you were supposed to do next? No one said hello. No sign directed you to “Order at the Window” or “Please seat yourself.” No directory on the wall pointed you to a visitor desk. Most guests in that situation will do one of three things: 1) they’ll wander around awkwardly and watch what other people do; 2) they’ll ask someone for help, or 3) they’ll turn around and leave.
Have you ever walked into a restaurant or other place of business, looked around, and had no idea what you were supposed to do next? No one said hello. No sign directed you to “Order at the Window” or “Please seat yourself.” No directory on the wall pointed you to a visitor desk. Most guests in that situation will do one of three things: 1) they’ll wander around awkwardly and watch what other people do; 2) they’ll ask someone for help, or 3) they’ll turn around and leave.
This is an obvious failure of the organization to accomplish the first technique of a strong visitor management process: recognizing that visitors will come to your organization and they will need tools to make the initial moments of that visit comfortable and pleasant. We all know it is easier to remember negative experiences. Visitors who feel confused, lost, or unwelcome may never want to return, and even worse, may tell others about their treatment.
People have an inherent need to be recognized. The first step of recognizing visitors can be easy as saying, “hello”, having a sign that reads “Welcome Visitors” or a welcome screen that informs visitors of their next step. Not every location needs to roll out the red carpet for visitors, but every location needs to acknowledge the visitors who do walk through the door.
Every organization has different ways of recognizing guests, and they range from very hands-on and labor-intensive, to reception automation. Some methods can be combined for maximum impact.
 Historically, the most common method used by organizations to make guests feel recognized was to use people. There are really three types of personnel employed to greet visitors.
Historically, the most common method used by organizations to make guests feel recognized was to use people. There are really three types of personnel employed to greet visitors.
Using people to greet guests has the advantage of bringing a personal touch to the welcome process. A warm smile, and a “how may I help you?” can provide the start to a truly positive experience.
On the other hand, using people is expensive. You have the direct cost of a dedicated receptionist who is paid primarily to greet guests. Or, if you prefer, you have the high cost of productivity lost for semi-dedicated and informal receptionists. And in the case where you have a less-than-effective receptionist – one who greets people gruffly because they are tired of being interrupted – the cost could be greater in terms of negative attitudes toward your organization.
Visitors don’t always want or need to talk to a person to feel welcome. Organizations can spare employees' time and save money by making effective use of the following methods for greeting guests.
Automated receptionists and signage have the advantage of being relatively permanent, tireless, and available 24 hours a day. The cost is far less than paying a dedicated person. Also, as crazy as it sounds, people don’t always like talking to people. Being able to use a kiosk or signage is often preferable to having to ask someone for directions. Signs and kiosks may not be able to deliver the warmth of a smile, but they can direct visitors to the person most likely to give them that smile.
You guessed it, there is no single "best way". Rather, the best option to greet guests varies by organization, but all of the most effective methods ensure that the guest is acknowledged, either by a sign or a smile. Visitors should feel welcome, and confident that they can accomplish what they came to do. Using forethought and planning, you can ensure your organization recognizes visitors as part of your visitor management process.
When visitors arrive at your place of work, how do you find out who they are and what their business is? Identifying visitors is an important step in the visitor management process. Once you have this valuable piece of information you can create a great visitor experience. Not having it though could cause you to steer a guest in the wrong direction, or allow someone onto the premise who should not be there.
In the prior section, we described how important it is to simply greet guests and make them feel comfortable. Once this is accomplished, the next step in the process is to determine who they are, what type of guest they are, and how best to meet their needs.
 Organizations have varying levels for how they need or want to greet guests, and it often depends on the type of business that person has come to accomplish. You might be thinking, “My organization doesn’t have many visitors,” but you’d be wrong. Even the most insular of organizations will have people show up from time to time. Consider the following types of visitors:
Organizations have varying levels for how they need or want to greet guests, and it often depends on the type of business that person has come to accomplish. You might be thinking, “My organization doesn’t have many visitors,” but you’d be wrong. Even the most insular of organizations will have people show up from time to time. Consider the following types of visitors:
 Once a visitor walks in the door, how do you find out what they need?
Once a visitor walks in the door, how do you find out what they need?
If you are employing a full-time receptionist to greet people, the logical next step is to ask the person who they are, and what they are there to accomplish. With a person at the door, a simple, “How may I help you?” will start the conversation, though other questions may be needed. Depending upon the security needs of your organization, you might require a guest to show an I.D., fill out forms, create a and explain their business.
What happens if the receptionist is busy on the phone when a guest arrives? Or if you don’t have a dedicated receptionist, and the person nearest the door is engaged in other tasks?
People aren’t the only way to ask guests what they need. More and more offices are using iPad receptionists to allow visitors to check-in themselves, whether they employ a receptionist or not. If the receptionist is tied up on the phone but can pause long enough to point a guest to an automated reception kiosk, the guest can continue the visitor registration process instead of waiting around. Guests of all kinds don’t like to wait and appreciate the ability to be proactive instead of inactive.
A reception application might ask the following questions:
Once the information is obtained, the receptionist or the kiosk can either direct the guest to the appropriate location or contact the appropriate person to come meet the guest.
Unless they are lost and only walked in to get directions to somewhere else, every visitor who enters your organization is there for a specific purpose. However, the person is greeted, finding out the reason for their visit is mission-critical to successfully moving them along on their journey. Your method for identifying them, whether a person or a digital visitor management system, needs to have the necessary skills to politely and effectively gather this key information. Then, they must be intelligent enough to guide the visitor to their next step.
Only after you have successfully identified the visitor and their purpose can both your visitor and your organization continue the tasks that keep you in business.
Does your organization require visitors to sign in upon arrival? Every organization, and even individual offices within, has different guidelines surrounding guests and whether or not signing guests in is part of their visitor management system.
In parts of this series detailing the visitor management process, we described different ways to greet and identify your guests. Once you’ve identified which type of person or group is standing in your lobby, it is time to determine how much of the check-in process they are required to complete.
Whether or not you have visitors sign a paper or digital visitor logbook will depend largely on the rules or customs of your organization, but there are definite benefits to requiring visitors to check-in.
 In today’s modern world, office security is a higher priority than ever before. Schools, government buildings, large firms, and factories all have reasons for knowing who is inside their facilities. And while businesses might like to maintain an open-campus type policy when it comes to visitors, that also makes them less secure.
In today’s modern world, office security is a higher priority than ever before. Schools, government buildings, large firms, and factories all have reasons for knowing who is inside their facilities. And while businesses might like to maintain an open-campus type policy when it comes to visitors, that also makes them less secure.
Visitors are wild cards. Security best practices require visitors to sign in, which acts as the first layer of protection from would-be criminals – people who would harm people or steal data – by causing them to have to think twice about leaving a trail of evidence.
Many organizations require employees to wear or carry identification that doubles as electronic access keys for buildings. Visitors might also need visitor badges in order to access areas, or simply for identification.
A good, secure sign-in process will require, at a minimum, the following information from guests:
To go above and beyond, some organizations might also require:
 It might seem slightly counterintuitive, but having visitors sign in can actually help them feel more welcome. While some visitors may be frustrated by having to jump through hoops, this technique is also a signal that your organization has taken visitors into consideration, and it gives guests the knowledge that they’ve come to the right place. When a guest signs in, they know you are aware of their presence and therefore they are less likely to be left wandering around.
It might seem slightly counterintuitive, but having visitors sign in can actually help them feel more welcome. While some visitors may be frustrated by having to jump through hoops, this technique is also a signal that your organization has taken visitors into consideration, and it gives guests the knowledge that they’ve come to the right place. When a guest signs in, they know you are aware of their presence and therefore they are less likely to be left wandering around.
Also, if visitor badges are part of the sign-in process, you can train your employees to keep an eye out for those visitors who might need a little extra help. Guests often find themselves lost in an unfamiliar location, especially if your building has a lot of twists, turns, and levels. Visitor badges give employees the immediate knowledge that the people wearing them are supposed to be in the building, but may not be familiar with the layout.
Not every organization is super-sensitive to security, and maybe not every visitor who comes in will be required to sign in. When thinking about your organization and its security needs, you’ll want to think about what your goals are, and what happens in your visitor management process. In step six of this article we will discuss the benefits of keeping a visitor registration log that includes all guests, but here are some possible questions to consider.
Whatever process you choose for signing in guests, visitors will appreciate any steps you take to make the experience easy. Take the time to plan ahead to determine your security needs and how best to make guests feel welcome. An efficient visitor sign-in process shows your guests that they are not just an afterthought, but rather an integrated part of a well-functioning workplace.
When any visitor arrives at your workplace, they are there to connect with a person. It might be their host for a meeting, one of the people who receive food or package deliveries, or someone they need to consult with. Helping the guest and their host connect is a crucial step in any visitor management process. There is nothing worse than walking into a building and talking to ten different people before you find someone who can actually help you. So how can you make this step seamless?
First, of course, you have to ensure you are first greeting guests, if necessary. Upon knowing their purpose, you can determine who they came to see; it may be a specific person, a group of people, a department, or even security if they are not wanted at your site.
What is a host employee’s job? And what are the mechanics of making sure the host knows their guest has arrived in a timely manner?
 When we think of a host, we often think of those who hold a dinner party, house guests or even travelers in their home, like Airbnb. The fact is, whenever an employee has someone come to see them at work, that employee is serving as a host. For however long the visitor is at your organization, that employee is the face of your organization. It is their responsibility to leave a good impression.
When we think of a host, we often think of those who hold a dinner party, house guests or even travelers in their home, like Airbnb. The fact is, whenever an employee has someone come to see them at work, that employee is serving as a host. For however long the visitor is at your organization, that employee is the face of your organization. It is their responsibility to leave a good impression.
Here are some basic reception etiquette tasks a host can do prior to a guest’s arrival to make sure their visitor has a good experience:
How you connect your visitors to your hosts will largely depend on how your reception area is staffed and what the practices of your organization are, but the mechanics are basic. One of the following things has to happen:
While the mechanics are simple, there are multiple consequences that could interfere with how work gets done and the impression guests get from your organization. The pros and cons hinge on whose responsibility it is to contact the host:
Perhaps the most fail-safe method of ensuring that guests and hosts get connected is to have a combination of a visitor check-in app supported by live staff for extenuating circumstances.
Real-time reception notifications connecting visitors with the appropriate host are vital to getting business done. You want your visitors to feel welcomed, and to leave with the impression that your office has its act together. Contacting their host quickly and efficiently allows everyone to get on with the important job of accomplishing the purpose of their visit.
Your visitor has arrived, been greeted, signed in, and has been connected with the appropriate host. When their business at your workplace is complete, what happens? Does your guest just walk out the door? Or is your visitor required to check out?
Throughout this series, we’ve been exploring the various steps to a good visitor management system and explaining why some easily overlooked steps and processes can important. Perhaps the most overlooked step of visitor management is visitor checkout. Unless you run a medical office or are in the hotel business, most organizations don’t focus on guests checking out; guests just leave. However, there is one very compelling reason to have guests check out: security.
 Security means protecting your people, physical assets, and data. When it comes to securing your workplace from the dangers of onsite visitors, you can’t know if a guest has left your premises unless the guest is required to check out. There are multiple security reasons for a visitor to actively check out of the location.
Security means protecting your people, physical assets, and data. When it comes to securing your workplace from the dangers of onsite visitors, you can’t know if a guest has left your premises unless the guest is required to check out. There are multiple security reasons for a visitor to actively check out of the location.
 How your visitors check out will largely depend upon how they check in. If a guest is writing their name on a paper visitor logbook upon checking in, then they might be required to write the time at which they check out next to their initial signature. If you have a large volume of guests checking in and out, this may require flipping through a number of pages and isn’t very efficient. Not to mention that every guest can see everyone else that has visited.
How your visitors check out will largely depend upon how they check in. If a guest is writing their name on a paper visitor logbook upon checking in, then they might be required to write the time at which they check out next to their initial signature. If you have a large volume of guests checking in and out, this may require flipping through a number of pages and isn’t very efficient. Not to mention that every guest can see everyone else that has visited.
If you have a staffed reception desk, the receptionist or security guard may check the visitor out, taking any physical objects, like keys or key cards, at that time. The staff person might be required to update the paper or electronic log, or to ask the visitor to do so.
Pointing visitors to an iPad receptionist for checkout is probably one of the most efficient ways to have them check out. This maintains easy-to-search electronic records of the visit. It also gives visitors some active role in the check-out process. It is a signal that their business is complete and they can transition to their next task accordingly.
The last time you went to an amazing restaurant, did you save room for dessert? Never underestimate the value of a great last impression.
Checking out of your facility is quite simply the final step a visitor ought to take before leaving your facility. With the stress of business complete, and all parties mentally recapping the visit or moving onto their next activities, it is easy to skip. Yet this important step in the visitor management process gives your organization a measure of security nearly impossible to achieve without it.
You thought that when the guest left the visitor management process was over? Not quite.
We all love visitors! It’s a chance to move your business or projects forward, to showcase your work, or even to take a respite from those!
When putting a process to your visitor management system, when a visitor to your organization has signed in, accomplished something amazing - or maybe just had lunch - with one of your staff, and then signed out... Do you keep the visitor log?
Over the course of this series, we’ve discussed all the important steps of having a visitor management process. The final piece of an efficient process occurs almost completely outside the visitor’s experience. While the visitor is aware of signing in and signing out, whether or not you keep a record of visitors is completely at the discretion of your organization. There are definite benefits to keeping a visitor log.
 There are some distinct advantages to keeping a visitor log. You never know when you might need to reference the information. Here are some possible reasons and scenarios.
There are some distinct advantages to keeping a visitor log. You never know when you might need to reference the information. Here are some possible reasons and scenarios.
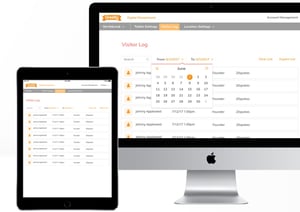 Most visitor logs are going to be in one of two forms: a paper log that people sign in and out of, or a digital record.
Most visitor logs are going to be in one of two forms: a paper log that people sign in and out of, or a digital record.
In our increasingly digital world, it is hard to believe that paper logbooks still exist. There are a number of drawbacks to paper visitor records.
Digital visitor logs, especially cloud-based, have several distinct advantages over paper logs.
When it comes to keeping organizational records, we often fall into two camps.
As is usually the case, the best scenario is somewhere in the middle: you may have reason to go back in the records two, five, or ten years, depending on your organization’s needs.
If you are keeping paper records, it is likely they will either be thrown out long before this or filed away in a manner that is unlikely to ever be retrieved. Digital records can be automatically archived or deleted after a certain length of time. Even if you choose never to delete the records, they take up so little space that keeping them will be no hassle at all.
Keeping a visitor log, preferably in digital form, is the final step in a comprehensive visitor management process. A guest is greeted, identified, signs in, meets up with the host, and signs out. Then, the log of these visits is filed away to the benefit of all the different parties who might have need of them. It is the final link in the chain of a successful visit and an efficient process.
You made it! You are now officially one of the world's foremost experts on visitor management techniques!
The pros and cons of different visitor management systems so you can determine the perfect plan for your workspace.
Walk into an office during the Mad Men era you would be greeted by a receptionist. See the latest tools for efficient and secure modern office...
Like every aspect of the modern office, visitor management software has evolved. From pen and paper to cloud-based reception management software